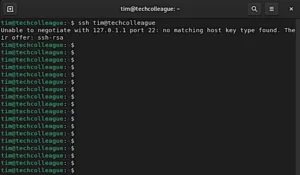
How to Fix kex_exchange_identification: connection closed by remote host
I recently encountered an issue connecting to a remote server via SSH. I got the following error message: “kex_exchange_identification: connection closed by remote host.” After some research and troubleshooting, I … Read more