If you use GPG for encryption, you may already be aware of the importance of these keys in keeping your messages secure. But have you considered setting an expiration date for your GPG key?
In this article, I want to share why this is such an important practice and what you need to know to implement it effectively.
Whether you’re an experienced GPG user or just getting started, this article will provide valuable insights and best practices for managing your GPG keys.
So, let’s dive in!
Understanding GPG Key Expiration
Let’s start by discussing GPG key expiration and why it’s important.
A GPG key expiration is a setting that allows you to specify a date and time when your GPG key will automatically become invalid.
This means that after the expiration date, you won’t be able to use your key to encrypt or sign messages, and anyone with your key will no longer be able to use it to encrypt messages to you.
The idea behind this feature is that your GPG key should have a limited lifespan, like a passport or a driver’s license.
The reason for this is that keys can be compromised or lost, and by having an expiration date in place, you can ensure that if this happens, the damage will be limited to a specific period.
Having a GPG key expiration also makes it easier to keep track of your keys and manage them regularly. This is because you’ll know exactly when each key will expire, and you can plan to renew or replace it well in advance.
Protecting your digital security is a must; GPG key expiration can greatly assist with that. Setting an expiration date for your GPG key limits the harm in case it ever gets hacked and helping yourself manage them more efficiently.
Now we’ll discuss how precisely you can set this deadline.
Setting an Expiration Date for Your GPG Key
Now that we understand the importance of GPG key expiration let’s look at how you can set an expiration date for your GPG key.
First, you’ll need to open your computer’s terminal or command line interface. If you’re unfamiliar with the terminal, don’t worry, I’ll walk you through the steps.
Once the terminal is open, you’ll need to generate a new key or edit an existing one.
To generate a new key, you can use the following command:
gpg --gen-keyTo edit an existing key, you’ll need to know the key ID. You can find this by using the following command:
gpg --list-keys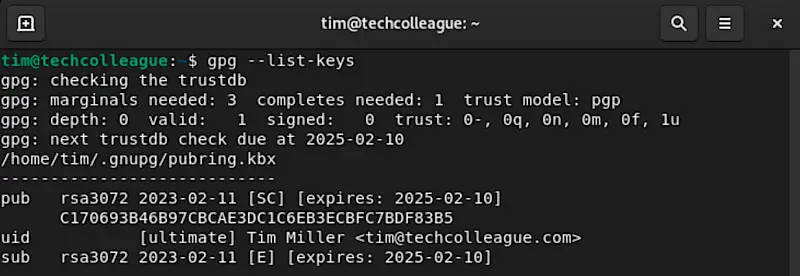
Once you have the key ID, you can edit it using the following command:
gpg --edit-key [KEY ID]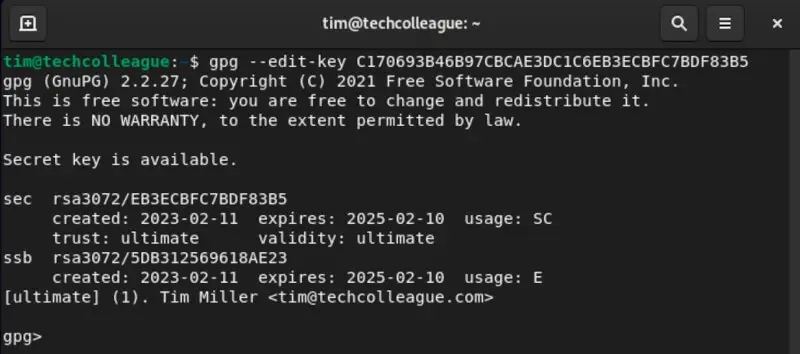
Once you’ve generated or located your key, you’ll need to set the expiration date. To do this, you’ll use the following command:
expire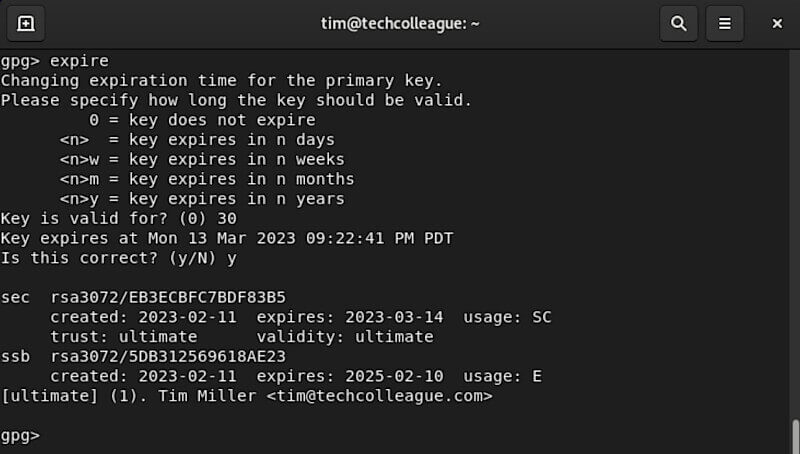
This will prompt you to enter the number of days until the key expires. You can also specify the date in the format YYYY-MM-DD.
It’s important to consider a few factors when setting an expiration date for your GPG key. First, you should choose a date that is far enough in the future to allow you to use your key for an extended period but not so far that you’ll forget about it.
Second, you should consider your key’s lifespan in relation to your usage. For example, if you use GPG regularly, you may want to set a shorter expiration date to rotate your keys more frequently.
Finally, it would be best to consider the security implications of your key expiration date. If you’re using your key for sensitive communications, you may want to set a shorter expiration date to reduce the risk of your key being compromised.
Choosing an expiration date for your GPG key is easy and can be done with just a few clicks in the terminal or command line interface. Before deciding on one, it’s important to consider aspects like usage rate, lifespan expectancy, and any security implications that could arise.
Once you’ve assessed all of these points, you’ll better know which expiration date works best for your needs.
Key Rotation and Renewal
Now that you know how to set an expiration date for your GPG key, let’s talk about key rotation and renewal.
Key rotation is replacing an old GPG key with a new one. This is an important practice because it helps you maintain the security of your digital communications by reducing the risk of your key being compromised.
To rotate your key, you’ll need to generate a new key, export your public key, and distribute the new key to your contacts. It would be best if you also revoked your old key to ensure it can no longer be used.
Key renewal is similar to key rotation, but instead of replacing your key with a new one, you extend the lifespan of your existing key. You’ll need to edit your key and set a new expiration date to renew your key.
It’s important to consider a few factors when deciding whether to rotate or renew your key. First, you should consider the security implications of your key.
If you’re using your key for sensitive communications, you may want to rotate it more frequently to reduce the risk of it being compromised.
Second, consider the effort required to rotate or renew your key. Key rotation requires more effort than key renewal because you’ll need to generate a new key, export your public key, and distribute the new key to your contacts.
Finally, it would be best if you considered the impact on your contacts. If you have many contacts who use your key, rotating your key can be a complex process that requires significant effort.
Ensuring the integrity of your digital communications is paramount, so key rotation and renewal are crucial. When selecting the most suitable approach to manage GPG keys, consider factors such as security ramifications, effort required, and its impact on those you communicate with.
Doing so will help ensure optimal safety in managing said keys.
Importance of Regular Key Management
Now that we’ve discussed setting an expiration date for your GPG key and key rotation and renewal let’s discuss the importance of regular key management.
Regular key management is critical to the security of your digital communications. By regularly reviewing and updating your keys, you can ensure that your keys are up-to-date and secure.
One important aspect of regular key management is monitoring the expiration dates of your keys. You should ensure your keys don’t expire before you can renew or rotate them.
Another important aspect of regular key management is monitoring the security of your keys. You should ensure that your keys are stored securely and have a backup in case your key is lost or damaged.
It’s also important to regularly update the information associated with your keys, such as your name, email address, and key fingerprints. This helps you make sure that your keys are accurate and up-to-date.
Regular key management also involves monitoring the keys of your contacts. You should ensure that your contacts use secure and up-to-date keys and that you have their latest ones on file.
Establishing a regular key management process is essential to protect your digital correspondence.
By diligently tracking and verifying all keys, including those from contacts, refreshing them as needed, and saving backups of each one– you can confidently guarantee that everything stays safe and current.
Conclusion
GPG key expiration is an important aspect of maintaining the security of your digital communications. By understanding the GPG key expiration, setting an expiration date for your key, and practicing key rotation and renewal, you can ensure your keys remain secure.
Regular key management is also critical to maintaining the security of your keys. You can ensure that your keys are always up-to-date and secure by monitoring the expiration dates of your keys, updating key information, and monitoring the keys of your contacts.
Overall, managing your GPG keys properly is essential to maintaining the security of your digital communications. Following the best practices outlined in this article can protect your privacy and secure your digital communications.





