The error “gpg: decryption failed: No secret key” does not mean your secret key has been compromised and your encrypted files are no longer secure. When you decrypt a file using GNU Privacy Guard (GPG), and no secret key is available.
When decrypting a file, GPG looks for a secret key in your public keyring. If it does not find one, then it will display an error message: “gpg: decryption failed: No secret key”. There is no secret key in your public key ring that matches your private key. Luckily, it’s an easy fix!
We have already created an in-depth guide on how to solve the “GPG decryption failed – no secret key” issues, with step-by-step instructions on how to solve this issue on Windows and Mac OS X machines.
What is GNU Privacy Guard (GPG)?
GNU Privacy Guard, also known as GPG, is a public key cryptography program that provides strong encryption of data and secure communication. GNU Privacy Guard is a GNU project and part of GNUtoolkit.
It’s an implementation of OpenPGP, which is described in RFC 4880, designed to make it easy to encrypt and sign your data and communication. It can also be used for other applications like file signatures and message authentication codes.
How to Fix “gpg: decryption failed: No secret key”?
The most likely reason for the “gpg: decryption failed: No secret key” error is that you need to import your public key so that other people can send you encrypted messages. You’ll have received a copy of your public key when you first generated it.
However, if you deleted that email, or accidentally deleted it from your inbox, then there’s no way for others to send you a message. Fortunately, fixing the “gpg: decryption failed: No secret key” error is easy.
Solution 1: Destroy the gpg-agent
Killing the GPG-agent process can help you recover from a gpg decryption failed error.
Here’s how to do so:
- Open a terminal window and check if the gpg-agent is running:
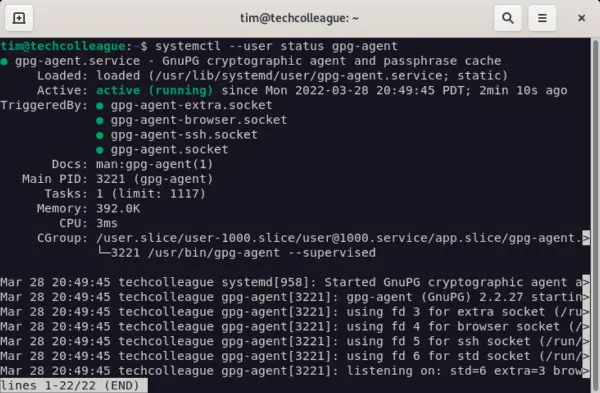
- This will show you if gpg-agent is running.
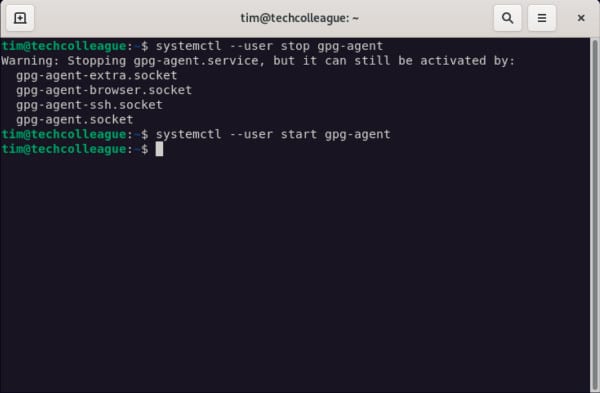
- You will need to stop the gpg-agent and then start it again.
Solution 2: Remove the GPG cache
When you try to decrypt a message, GPG checks your cache for a public key match. If it doesn’t find one, it shows you an error message. This is another reason why “gpg: decryption failed: No secret key” occurs in some cases.
To clear the GPG cache, open a terminal window and enter the following command:
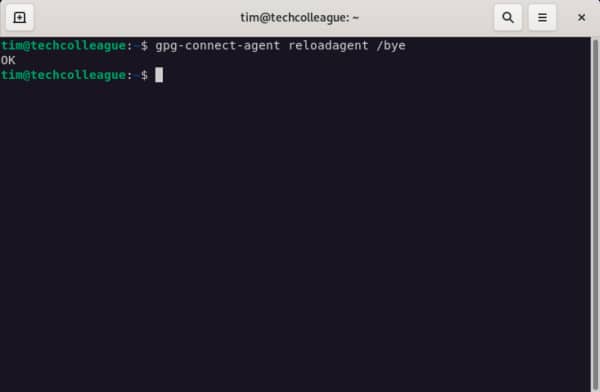
Then try decrypting again.
Solution 3: Install and Configure pinentry-tty
Sometimes, “gpg: decryption failed: No secret key” occurs when your system is trying to talk to GnuPG but doesn’t recognize it.
“pinentry-tty” is a program that allows you to enter a passphrase or PIN with GPG securely.
To fix this problem, follow these steps:
- First install pinentry-tty by running the following command:
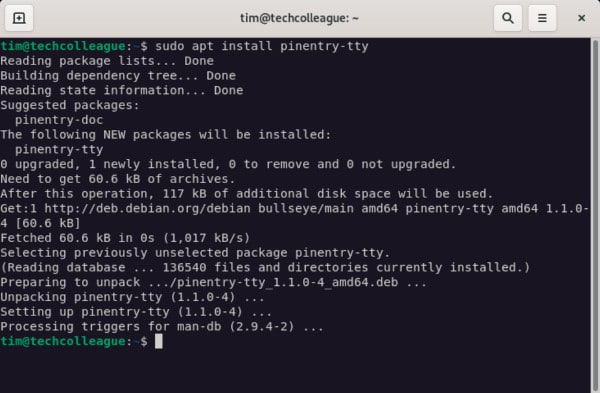
- Set “pinentry-tty” to be the default program for gpg-agent by updating the gpg-agent.conf file. The gpg-agent.conf file should be blank.
sudo nano ~/.gnupg/gpg-agent.conf - Add the following line to this configuration file.
pinentry-program /usr/bin/pinentry-tty- After adding this line, save this file by pressing Ctrl-O and then press Ctrl-X to exit the nano editor.
- Reload the gpg-agent so the changes take effect.
gpg-connect-agent reloadagent /byeThe GPG decryption should be working now.
Solution 4: Export and Upload the Personal Key
Before you start fixing the “gpg: decryption failed: No secret key” error, it might be helpful to export your public key and upload it to a keyserver.
This step can help fix a handful of different problems that cause decryption errors, including issues with the GPG cache. When exporting your key, you’ll need your passphrase.
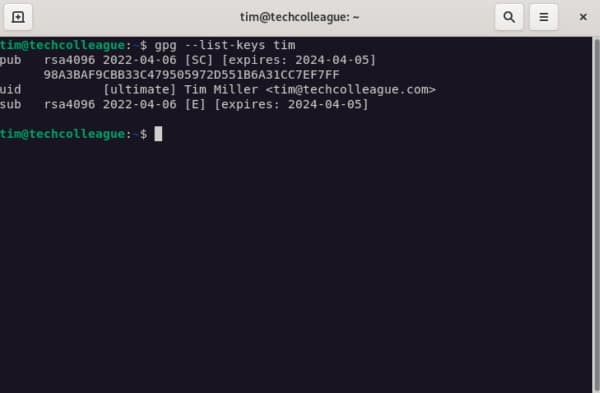
Run the following command to list your GPG keys:
gpg --list-keys <user-id>For an example of user ID tim, see the output below:
To export the GPG secret key, run the following command:
gpg --export-secret-keys <user-id> > private.keyTo import the GPG secret key on another user, run this command:
gpg --import private.keyFor an example of the import for user ID tim, see the output below:
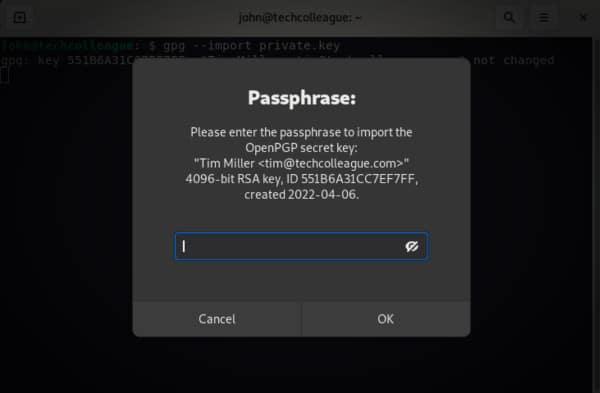
Provide the passphrase that was used for the user ID.
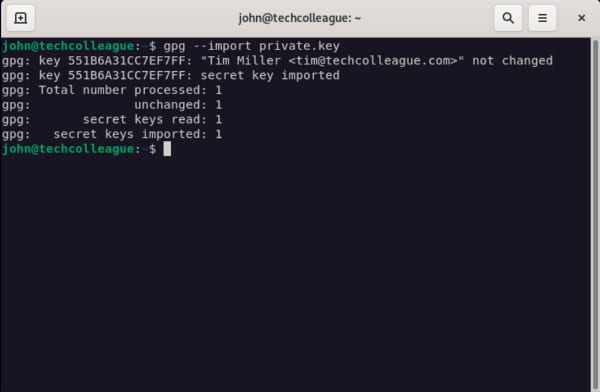
After the GPG secret key has been imported, the “gpg decryption failed no secret key” error should go away.
Solution 5: Set up the GPG Key Trust Level
Another problem that causes the “gpg: decryption failed: No secret key” error is that your GPG key isn’t correctly set up for encryption or signing.
To fix it, you’ll need to edit your key. Follow these steps:
- Open a terminal window and enter the following command:
gpg --edit-key [your user ID]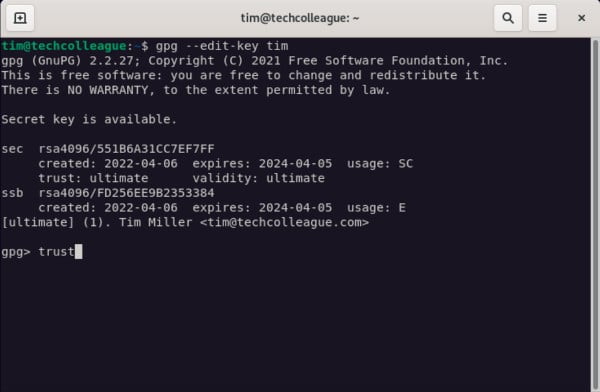
- At the bottom of your screen, type trust and press Enter.
- A menu will appear. At the gpg prompt, type 5 to set I trust ultimately.
- Exit the gpg menu by typing quit.
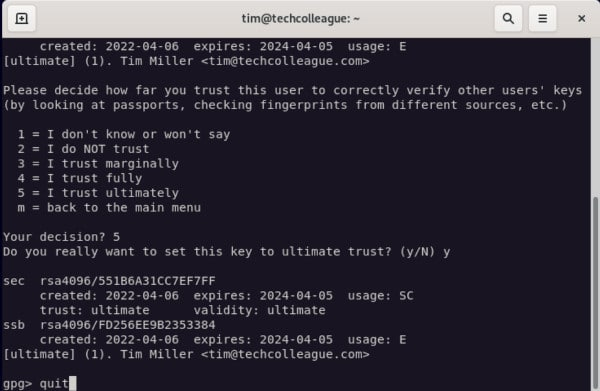
Finally, try decrypting again.
Solution 6: Update the GPG Software
If all else fails, update your version of GPG by running these commands in the terminal:
sudo apt-get update
sudo apt-get upgrade
sudo apt-get dist-upgrade
sudo apt-get auto-remove
sudo apt-get autocleanThen reboot your computer and try decrypting again.
Frequently Asked Questions
Can You Decrypt a GPG Without a Key?
No, you need a private key to decrypt GPG but you can use the GPG command to find out which key has been used for encryption.
gpg --list-packetsIf you encrypted it with your public key that’s supported by GPG, then yes, you can encrypt it without a key.
What Does No Secret Key Mean?
“No secret key” means that the GPG message has been not been encrypted for a key that you own a private key. If you do not have any private keys, it is impossible to decrypt such messages.
If someone else owns a private key corresponding to your public key, they can decrypt your messages.
Can I Decrypt My Own Message?
No, you cannot decrypt your own message. If you have a private key, it is not possible to decrypt your own message. You need to have encrypted it with your personal public key to do that.
Can End-to-End Encryption Be Hacked?
No. There’s no party that can access your encrypted data except you the recipient and the sender. Hackers and third parties cannot decrypt messages.
Even if a third party eavesdrops on your encrypted messages, they will not be able to access them because they do not own your private key and cannot decrypt such data.
Where are GPG Public Keys Stored?
GPG public keys are stored in keyring files. These files can be located in your ~/.gnupg directory or a directory specified by your GNUPGHOME environment variable. By default, GPG uses a file named pubring.gpg to store your public keys.
This file should not be edited directly because it is automatically managed by GPG. Instead, you should use “gpg –import” to add new keys and “gpg –export” to remove them from your keyring.
Conclusion
While solutions can vary, many problems related to GPG decryption failure can be resolved by simply making sure your public and private keys are set up correctly in your system. This guide should help you get up and running with encryption.
If you’re still experiencing trouble decrypting messages, make sure you check for updates for your software before getting in touch with a professional.