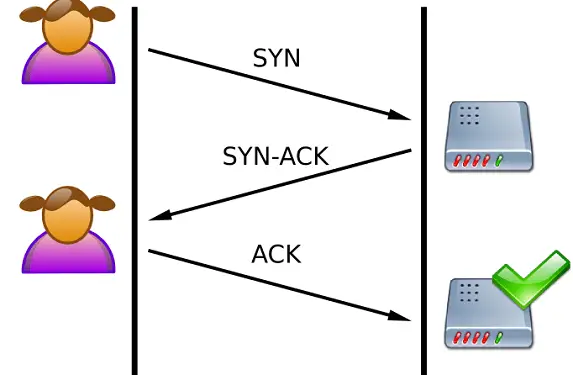
When a DoS attack ack scan occurs, an attacker will send a large number of SYN packets to a victim’s machine. The victim’s machine will then respond with an SYN-ACK packet for each one of the attacker’s SYN packets.
However, since the attacker never responds to the victim’s SYN-ACK packets, the victim’s machine will eventually time out and close the connection. This can cause the victim’s machine to become overloaded and unusable.
What is a DoS Attack: ACK Scan?
A Denial of Service (DoS) attack is an attempt to make a machine or network resource unavailable to its intended users.
Although the means to carry out, motives for, and targets of a DoS attack may vary, it generally consists of the concerted efforts of a person or persons to prevent an Internet site or service from functioning efficiently or at all, temporarily or permanently.
One type of DoS attack is called an ACK scan. This type of attack works by sending a large number of ACK (acknowledgment) packets to a target machine. These ACK packets are spoofed to appear as if they come from a legitimate source.
When the target machine receives these packets, it responds with an RST (reset) packet, which tells the sending machine to stop sending data.
If enough ACK packets are sent, the target machine will eventually be overwhelmed and unable to process legitimate traffic. This can cause the machine to crash or become unresponsive.
ACK scans are relatively easy to carry out and can be very effective. However, they are also relatively easy to detect and defend against. A good defense against an ACK scan is a firewall that can detect and block these packets.
How To Stop DoS Attack ACK Scan?
There are a few ways to protect against DoS attack ACK Scans:
- Use a firewall: A firewall can block the attacker’s SYN packets from reaching the victim’s machine.
- Use SYN cookies: SYN cookies are a way to track valid connections. When a victim’s machine receives an SYN packet, it will respond with an SYN-ACK packet that contains an SYN cookie. The attacker’s machine must return the SYN cookie to complete the connection.
This way, the victim’s machine can keep track of which SYN packets are part of a valid connection and which ones are from an attacker.
- Use rate-limiting: Rate-limiting can limit the number of SYN packets a machine can send in a given period. This can help prevent an attacker from flooding a victim’s machine with SYN packets.
- Use anti-spoofing measures: Anti-spoofing measures can prevent an attacker’s machine from impersonating a victim’s machine. This can be done by filtering traffic based on the source IP address or by using cryptographic methods to verify the identity of a machine.
- Use an intrusion detection system: An intrusion detection system can be used to detect when an attacker is flooding a victim’s machine with SYN packets. This can help to identify an attack early and take steps to mitigate it.
How DoS Attack is Detected?
There are several methods to detect DoS attacks. Some require special hardware or software, while others can be performed with basic network equipment.
- Checking error rates: One way to detect DoS attacks is to check for an increase in the rate of errors on the network. This can be done by looking at the number of packets that are being dropped or corrupted.
- Checking for unusual traffic patterns: You can also look for unusual traffic patterns that might indicate a DoS attack. This can include a sudden increase in traffic from a particular IP address or a decrease in traffic from a normally busy network.
- Checking logs: Another way to detect DoS attacks is to check server logs for unusual activity. This can include a sudden increase in login attempts or a decrease in response time from the server.
- Using intrusion detection systems: Intrusion detection systems (IDS) can be used to detect DoS attacks. These systems monitor network traffic and look for signs of an attack.
- Using security appliances: Some security appliances, such as firewalls and load balancers, can be used to detect and block DoS attacks.
What Are the Different Types of DoS Attacks?
There are several different types of DoS attacks. Some of the most common include:
- SYN Flooding: This attack is used to overload a server with SYN requests. This can eventually cause the server to crash.
- Ping of Death: This attack involves sending a ping request larger than the maximum size allowed. This can cause the target system to crash.
- DNS Amplification: This attack amplifies the data sent to a DNS server. This can overload the server and cause it to crash.
- Smurf Attack: This attack involves sending many ICMP requests to a network to flood it. This can cause the target system to crash.
- Buffer Overflow: This attack involves sending more data to a system than it can handle. This can cause the system to crash or allow the attacker to take control of it.
Why are DoS or DDoS Attacks Carried Out?
There are many reasons why DoS or DDoS attacks are carried out. Most often, the attacks are politically motivated, and the attackers want to send a message or disrupt the operations of a particular organization.
Sometimes, the attacks are carried out for financial gain, as the attackers may demand a ransom from the victim organization in exchange for stopping the attack. In other cases, the attacks may be carried out simply for the attacker’s amusement or to prove a point.

How To Prevent DoS Attacks On Router?
If you get hit by a DoS attack, the attacker is likely spoofing the source IP address of their requests. This makes it hard to block the attacker’s IP address since it’s probably not the real one.
There are various ways you can use to prevent the Dos attacks on your router, which include:
- Use a firewall: A firewall can help to protect your network from DoS attacks by filtering incoming and outgoing traffic and blocking malicious requests.
- Enable router security features: Many routers have built-in security features that can help to protect against DoS attacks. These features may include packet filtering, access control lists (ACLs), and rate-limiting.
- Keep your router software up to date: Regularly updating your router’s firmware can help to protect against known vulnerabilities that attackers could exploit.
- Use a VPN: A VPN can help encrypt your traffic, making it more difficult for attackers to spoof your IP address and launch a DoS attack.
- Monitor your network activity: Keeping an eye on your network traffic can help you to spot a DoS attack as it’s happening and take appropriate action.
- Use a DDoS protection service: A DDoS protection service can help absorb the brunt of a DDoS attack and keep your network online.
What Can I Do to Prevent DDoS Attacks?
There’s no guaranteed way to prevent DDoS attacks altogether. However, you can take steps to minimize the risk of becoming a target and minimize the damage if you become a victim.
- It’s important to understand what DDoS attacks are and how they work clearly. This will help you to identify potential vulnerabilities in your systems and to put together a plan for how to respond in the event of an attack.
- You should take steps to secure your systems against common attack vectors. This includes ensuring that your network infrastructure is properly configured and your servers are properly configured and patched.
- You should consider using a DDoS protection service. These services can help mitigate the effects of DDoS attacks and give you peace of mind knowing that your systems are protected.
- You should have a plan in place for how to respond to a DDoS attack. This plan should include steps for identifying an attack, mitigating the effects, and recovering from the attack.
What Are the Penalties for a DDoS Attack?
There are several potential penalties for launching a DDoS attack, including:
- Civil damages: If you launch a DDoS attack that results in damages, you may be sued by the affected party and ordered to pay damages.
- Criminal charges: In some cases, DDoS attacks may be prosecuted as crimes, with perpetrators facing criminal charges and possible prison time.
- Fines: Depending on the severity of the attack, you may also be subject to fines from your ISP or other internet service providers.
- Reputational damage: DDoS attacks can also damage your reputation, making finding future employment or business partners difficult.
What is DDoS in Gaming?
DDoS in gaming is a cyber-attack that entails flooding a server or network with requests, making it difficult or impossible for legitimate users to access the resources they need.
This can be done by using a botnet, a group of computers that have been infected with malware and can be controlled remotely by the attacker. The attacker will then use the botnet to send a large number of requests to the target server or network, overloading it and causing it to shut down.
DDoS attacks are often used to target online gaming servers, as they can be overwhelmed by the number of requests and shut down.
This can be frustrating for legitimate users who are trying to play the game, as well as the game’s developers and administrators.
There are a few ways to protect against DDoS attacks, including firewalls and rate-limiting. However, the best method to protect against DDoS attacks is to possess a reliable cyber security plan in place.
This should include having a backup server or network, as well as having a response plan for when an attack does occur.
Cyber security is important for all businesses, but it is especially important for businesses reliant on online services. DDoS attacks can cause significant financial damage, as well as reputational damage. For this reason, it is important to have a good cyber security plan in place to protect your business from these types of attacks.
Frequently Asked Questions
Can Firewall Prevent DDoS Attack?
A firewall can’t prevent a DDoS attack, but it can help mitigate the effects of an attack. By blocking or rate-limiting incoming traffic from known malicious IP addresses, a firewall can reduce the traffic that reaches your servers.
This can buy you some time to respond to the attack and take steps to mitigate it.
However, a firewall won’t do anything to stop an attacker from targeting your IP address. If the attacker is using a botnet of infected computers, the firewall won’t be able to stop the attack unless it can block all of the IP addresses in the botnet – which is unlikely.
Do Netgear Routers Have DDoS Protection?
Netgear routers do not have DDoS protection, but there are some things you can do to minimize the effects of a DDoS attack on your network. One is to ensure that your router’s firmware is up to date, as this can help mitigate some of the potential effects of an attack.
Additionally, you can contact your ISP to see if they have any recommendations for dealing with a DDoS attack. Finally, it’s also a good idea to have a backup plan in place in case an attack takes your router offline.
Do Nighthawk Routers Have DDoS Protection?
If you’re looking for a router with top-of-the-line security features, you’ll want to consider a Nighthawk router. Nighthawk routers are powerful security tools to protect your home network from online threats. One of the most important security features is DDoS protection.
DDoS, or Distributed Denial of Service, attacks are cyber-attack that can cripple a home network by overwhelming it with traffic. A DDoS attack can come from a single individual or a group of attackers. Nighthawk routers have built-in DDoS protection to help defend against these attacks.
When a DDoS attack is detected, the Nighthawk router redirects traffic away from the affected device. This helps to prevent the attack from taking down your entire network.
Nighthawk routers also have advanced security features like VPN support and malware protection. A Nighthawk router is a good option if you’re concerned about online security.
How Long Do DDoS Attacks Last?
DDoS attacks can last for various lengths of time, depending on the type and severity of the attack. A smaller, less severe attack may only last a few hours, while a larger, more severe attack can last for days or weeks. The longest recorded DDoS attack lasted for over two months.
There are a few different factors that can affect how long a DDoS attack lasts. The type of attack can play a role, as different types of attacks may have different durations. The size and severity of the attack can also be factors, as larger, more severe attacks are likely to last longer than smaller ones.
Additionally, the resources and defenses of the target can play a role in how long an attack lasts, as a target with more resources may be able to withstand an attack for longer.
Ultimately, the length of a DDoS attack can vary depending on several factors. The attack’s type and severity, the target’s size, and the target’s resources can all affect how long an attack lasts.
What Are the Penalties for a DDoS Attack?
The penalties for a DDoS attack depend on the severity of the attack and the damages caused. The penalties may be minimal if the attack is small and does not cause significant damage. However, the penalties can be much more severe if the large attack causes significant damage.
Sometimes, a DDoS attack may even be considered a felony offense.
The best way to avoid the penalties associated with a DDoS attack is to prevent the attack from happening in the first place. This can be done by ensuring your network is properly protected and aware of the signs of an impending attack.
If you experience a DDoS attack, it’s important to have a plan in place to mitigate the damage.
Conclusion
Your computer’s security is at risk if you don’t have a firewall enabled. A DoS attack can overload your computer’s resources, making it difficult or impossible to access your computer. By understanding the types of DoS attacks, you can take steps to protect your computer.
You need to be particularly cautious about accepting unsolicited email attachments, as these can often contain malware that can launch a DoS attack.